Been a while - sorry about that! Life is quite busy, since my last post I've started a new job, which has had me very much engaged on a daily basis.
While I am in no way an expert, I have had the opportunity to work in a very large SOC(25+ Tier 1-3 analysts, 50+ engineers) as well as start one from the ground up.
One question that has been bugging me lately is how to do we determine how much staff we need?
Talent is very hard to find, so getting your number right could both save on labor costs and time.
We all know the pyramid style approach: Tier 1 on the bottom, tackling the false positives and easy tickets, these are you fresh out of school types, which make up most of the SOC, Tier 2 is somewhere in the middle less than Tier 1 but more than Tier 3 in terms of numbers. Tier 2 would handle some of the more labor intensive tickets, that may require some advanced knowledge of how the network is configured. Tier 3 on top handling the confirmed infections, possibly performing forensics on hosts to determine root cause, and then feeding the intelligence gathered to Threat Intelligence teams/platforms.
Unfortunately there is no formula for determining SOC size, as it depends on a number of factors:
Duties of a SOC, size of the organization in both personnel and endpoints, equipment found on the network, automation already in network etc...
One good place to start especially for smaller organization and companies is to team with an Managed Security Service Provider or MSSP. Have the MSSP handle the Tier 1 and 2 events, while an internal team handles confirm unresolved infections as well as other projects that may come up, such as product purchasing, configuring of network hardware, vulnerability scanning etc...
Executive buy in is very important, Executives that understand the need for security in an organization can certainly help grow and nurture the a fledgling SOC. It is important that executives understand that it is a marathon, not a sprint, that rewards an organization with a excellent security posture.
In the beginning analysts should be expected to wear many hats. One analyst may be in charge of a purchase project, vulnerability scanning, tickets, which could include a forensic investigation, as well as performing engineering tasks for the networks firewalls. Once a security engineer or architect is hired, they will be expected to take over the firewalls, or purchase projects.
How to know when you have too much staff, too little.
Every organization is different, however, a IR team should be no less than 3 analysts, to begin. This allows for on/off weeks, vacation time, sickness etc.. Once established, as the manager of a SOC you should be talking to you people about workload regularly. If analyst are feeling rushed due to metrics or ticket load, consider hiring additional staff, if budgeting will allow.
"But Sol I dont have the funding to hire one much less three additional staff members, and my IR team is drowning in tickets. What should I do?"
There are a few things that I would address here.
1. What is the main reason your teams workload is so high, and find a way to either automate it, or pass it off to another team (like IT Support if able). Consider making changes to the network that will help mitigate threats. There is something from an engineering standpoint that may need to be done.
2. Labor issues, its no secret that cyber security talent is expensive. Wages are high, the training is expensive. Is there a major university in your area? Consider bringing on some students as interns. While their labor would be relatively unskilled, you could delegate some tasks to them which would assist your analysts; while also giving them some extremely valuable on-the-job training.
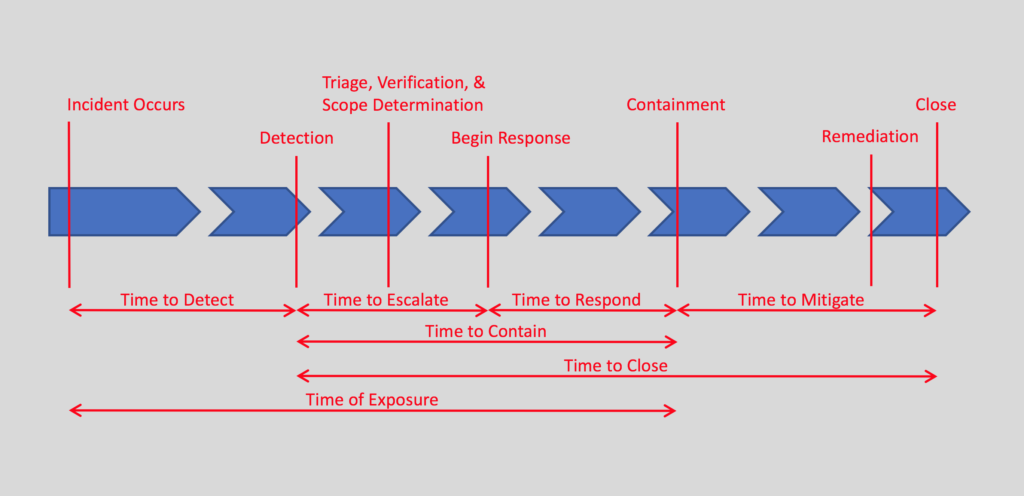
Metrics:
(credit: TAKSATI - Metrics That Matter)
This image is a great reference for the wide variety of metrics. If starting a new SOC, I would suggest not really worrying about metrics for the first year at least, processes are still being defined, analysts are still getting used to the environment. It can be difficult to get an accurate reading on where the SOC stands.
Thats it for now. More soon.
While I am in no way an expert, I have had the opportunity to work in a very large SOC(25+ Tier 1-3 analysts, 50+ engineers) as well as start one from the ground up.
One question that has been bugging me lately is how to do we determine how much staff we need?
Talent is very hard to find, so getting your number right could both save on labor costs and time.
We all know the pyramid style approach: Tier 1 on the bottom, tackling the false positives and easy tickets, these are you fresh out of school types, which make up most of the SOC, Tier 2 is somewhere in the middle less than Tier 1 but more than Tier 3 in terms of numbers. Tier 2 would handle some of the more labor intensive tickets, that may require some advanced knowledge of how the network is configured. Tier 3 on top handling the confirmed infections, possibly performing forensics on hosts to determine root cause, and then feeding the intelligence gathered to Threat Intelligence teams/platforms.
Unfortunately there is no formula for determining SOC size, as it depends on a number of factors:
Duties of a SOC, size of the organization in both personnel and endpoints, equipment found on the network, automation already in network etc...
One good place to start especially for smaller organization and companies is to team with an Managed Security Service Provider or MSSP. Have the MSSP handle the Tier 1 and 2 events, while an internal team handles confirm unresolved infections as well as other projects that may come up, such as product purchasing, configuring of network hardware, vulnerability scanning etc...
Executive buy in is very important, Executives that understand the need for security in an organization can certainly help grow and nurture the a fledgling SOC. It is important that executives understand that it is a marathon, not a sprint, that rewards an organization with a excellent security posture.
In the beginning analysts should be expected to wear many hats. One analyst may be in charge of a purchase project, vulnerability scanning, tickets, which could include a forensic investigation, as well as performing engineering tasks for the networks firewalls. Once a security engineer or architect is hired, they will be expected to take over the firewalls, or purchase projects.
How to know when you have too much staff, too little.
Every organization is different, however, a IR team should be no less than 3 analysts, to begin. This allows for on/off weeks, vacation time, sickness etc.. Once established, as the manager of a SOC you should be talking to you people about workload regularly. If analyst are feeling rushed due to metrics or ticket load, consider hiring additional staff, if budgeting will allow.
"But Sol I dont have the funding to hire one much less three additional staff members, and my IR team is drowning in tickets. What should I do?"
There are a few things that I would address here.
1. What is the main reason your teams workload is so high, and find a way to either automate it, or pass it off to another team (like IT Support if able). Consider making changes to the network that will help mitigate threats. There is something from an engineering standpoint that may need to be done.
2. Labor issues, its no secret that cyber security talent is expensive. Wages are high, the training is expensive. Is there a major university in your area? Consider bringing on some students as interns. While their labor would be relatively unskilled, you could delegate some tasks to them which would assist your analysts; while also giving them some extremely valuable on-the-job training.
Metrics:
(credit: TAKSATI - Metrics That Matter)
This image is a great reference for the wide variety of metrics. If starting a new SOC, I would suggest not really worrying about metrics for the first year at least, processes are still being defined, analysts are still getting used to the environment. It can be difficult to get an accurate reading on where the SOC stands.
Thats it for now. More soon.

Comments
Post a Comment